The automotive industry is well known for its security standards regarding the road safety of vehicles. All processes regarding vehicle development – from drawing board to sales – were standardized and refined over the years. Both internal tests, as well as globally renowned companies like NHTSA or EuroNCAP, are working hard on making the vehicle safe in all road conditions – for both passengers and other participants of road traffic.
ISO/SAE 21434 – new automotive cybersecurity standard
Safety engineering is currently an important part of automotive engineering and safety standards, for example, ISO 26262 and IEC 61508. Techniques regarding safety assessment, like FTA (Fault Tree Analysis), or FMEA (Failure Mode and Effects Analysis) are also standardized and integrated into the vehicle development lifecycle.
With the advanced driver assistance systems starting to be a commodity, the set of tests started to quickly expand adapting to the market situation. Currently, EuroNCAP takes into account automatic emergency braking systems, lane assist, speed assistance, or adaptive cruise control. The overall security rating of the car highly depends on modern systems.
But the security is not limited to crash tests and driver safety. In parallel to the new ADAS systems, the connected car concept, remote access, and in general, vehicle connectivity moved forward. Secure access to the car does not only mean car keys but also network access and defense against cybersecurity threats.
And the threat is real. 6 years ago, in 2015, two security researchers hacked Jeep Cherokee driving 70mph on a highway by effectively disabling its breaks, changing the climate control and the infotainment screen display. The zero-day exploit allowing that is now fixed, but the situation immediately caught the public eye and changed the OEMs mindset from “minor, unrealistic possibility” to “very important topic”.
There was no common standard though. OEMs, Tier1s, and automotive software development companies worked hard to make sure this kind of situation never happens again.
A few years later other hackers proved that the first generation of Tesla Autopilot could be tricked to accelerate over the speed limit by only slightly changing the speed limit road sign. As a result, discussion about software-defined vehicles cybersecurity sparked again.
All of these resulted in the definition of the new standard called ISO 21434 “Road vehicles — cybersecurity engineering. The work started last year, but currently, it’s at the “Approval” phase, so we can quickly go through the most important topics it tackles.
In general, the new norm provides guidelines for including cybersecurity activities into processes through the whole vehicle lifecycle. The entire document structure is visualized below:
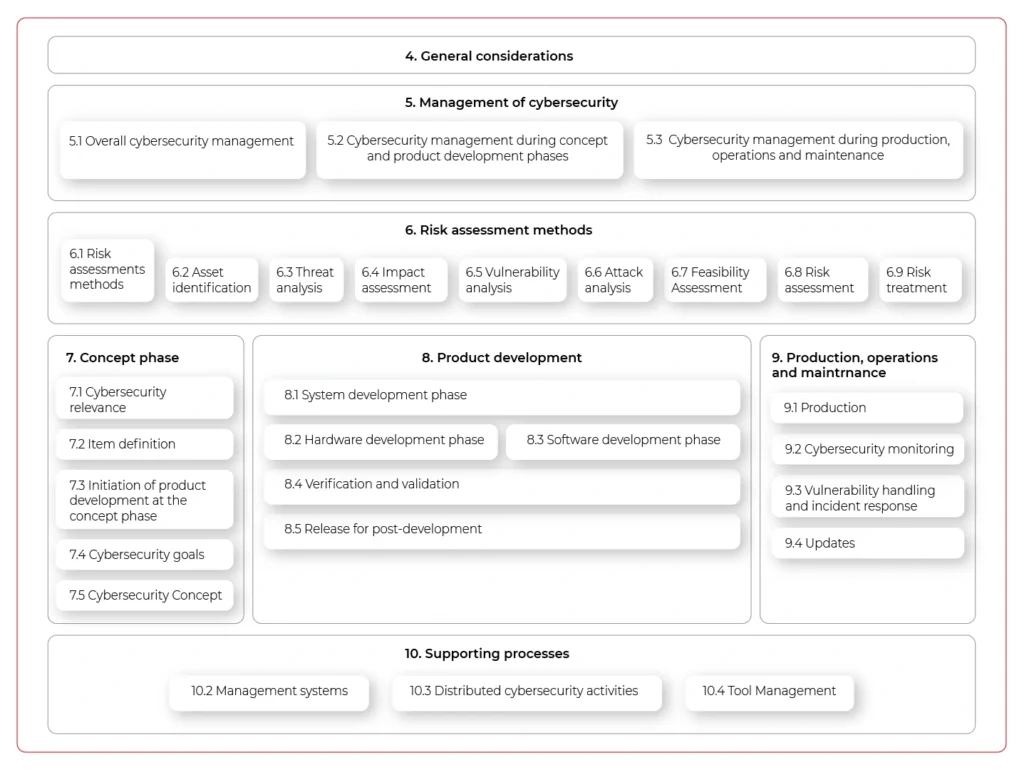
The important aspect of the new standard is that it does not only handle vehicle production but all activities until the vehicle is decommissioned – including incident response or software updates. It does not just focus on singular activities but highly encourages the continuous improvement of internal processes and standards.
The document also lists the best practices regarding cybersecurity design:
- Principle of least privilege
- Authentication and authorization
- Audit
- E2E security
- Architectural Trust Levels
- Segregation of interfaces
- Protection of Maintainability during service
- Testability during development (test interface) and operations10.
- Security by default
The requirements do not end on the architectural and design level. They can go as low as the hardware (identification of security-related elements, documentation, and verification for being safe, as they are potential entry points for hackers), and source code, where specific principles are also listed:
- The correct order of execution for subprograms and functions
- Interfaces consistency
- Data flow and control flow corrections
- Simplicity, readability, comprehensibility
- Robustness, verifiability, and suitability for modifications
The standard documentation is comprehensive, although clearly visible in the provided examples rather abstract and not specific to any programming languages, frameworks, and tools. There are recommendations, but it’s not intended to answer all questions, rather give a basis for further development. While not a panacea to all cybersecurity problems of the industry, we are now at the point when we need standardization and common ground for handling security threats in-vehicle software and connectivity, and the new ISO 21434 is a great start.






More Stories
Watch Adam Savage Go “Hands On” With the Original Enterprise From ‘Star Trek’ – Review Geek
Google Messages reactions about to expand in choices
Get a 2nd-Gen Apple Pencil for the Lowest Price Ever